# Password Policy
To enhance the security of the system and help it pass the compliance review, Root and system admin can set password policies that are valid to all members of the systems in [system settings-security center-password policy], including password strength, expiration, and password retry limit.
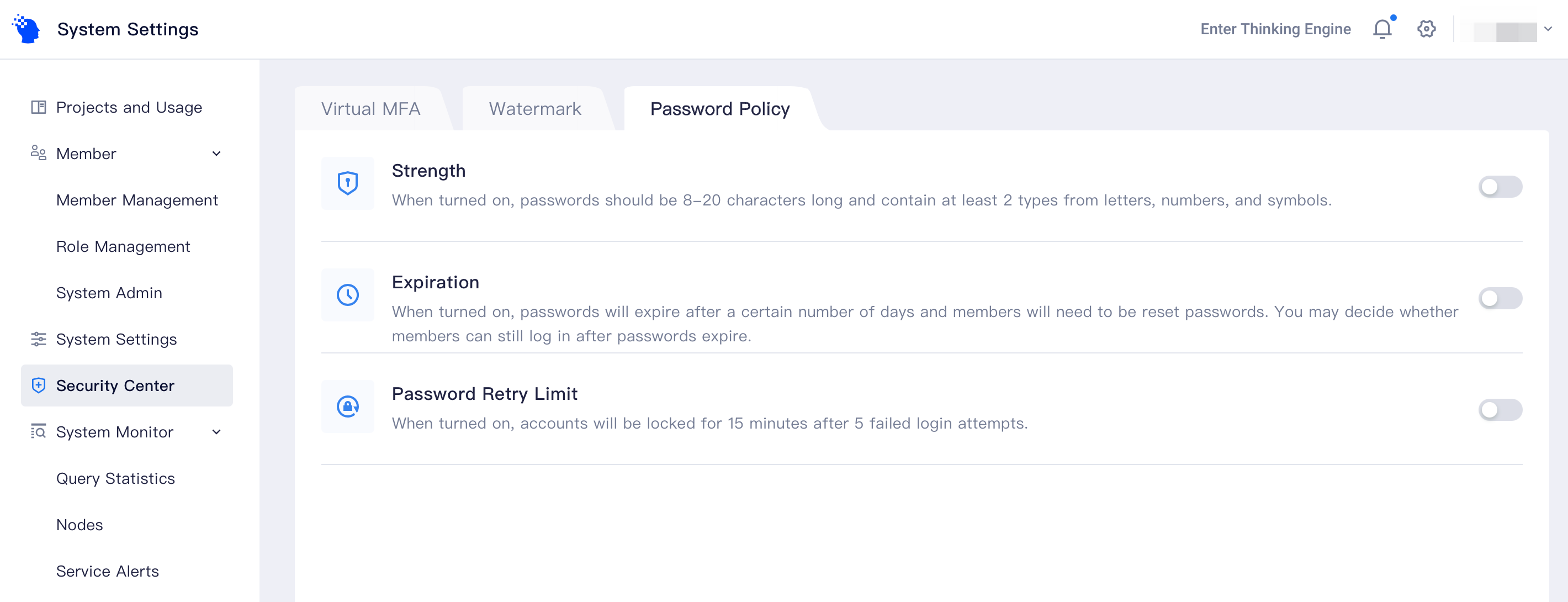
# Strength
After the "password strength" verification is enabled, the system would detect the password strength upon the next login of members. If the password strength does not conform to the requirements, the system would force members to modify the password after they log in successfully, otherwise, members would not be allowed to use the TE system.
After the password strength verification is enabled, it is required that the password shall contain 8-20 characters, including two of such elements as letters, numbers, and special characters. Special characters include English characters~`! @#$%^&*()+=_-{}[]":;"'?/<>,.. Space shall not be used as a part of the password.
# Expiration
Expiration refers to the upper limit of the interval between the two password modifications by each member. The validity period of passwords should be updated after each member's password modification. After enabling password expiration, members should modify the password before the expiration date. The system will notify members after they have logged in to modify the password 5 days before the expiration date.
Members could customize expiration policy in two ways: the validity period of passwords could be set as 1-1024 days; whether to enable "login after expiration". If "login after expiration" is enabled, members would be allowed to log in to the system with an expired password for once and be forced to modify the password after logging in to the system successfully. If the function is disabled, members can only activate their accounts by having the root admin modify their password and update the expiration date of the password.
# Password Retry Limit
Password retry constraints could be enabled to avoid brute force cracking of passwords. If a member has input the wrong password five consecutive times at a random time upon login, the account involved would be locked for 15 minutes. 15 minutes later, the member would try to log in with the password again. Members who have forgotten their passwords could ask the root admin to reallocate passwords for them.
